Most Whatsapp Dual SIM owners complain against the lack of DUAL-SIM Support for Whatsapp. I found two neat solutions working on most Android smartphone
Solution 1: Add a second user
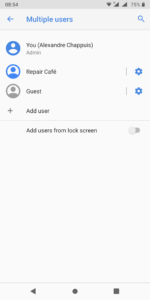
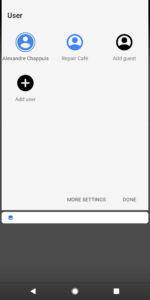
Most Android smartphones support multiple users. In order to use Whatsapp, you will have to add a second user on your smartphone and add a new Google Play Account.
From the Administrator user, you must grant some privileges to access SMS and the telephone. Here’s an example to administrate Whatsapp for the association “Repair Café Fribourg”


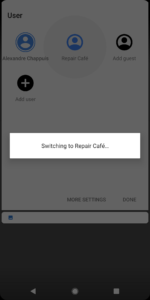

Advantages
- Whatsapp works for each user account, data is clearly separated
- The switch between the two users is efficient
- The second SIM is only used for the activation. It’s OK to use the same SIM card for data connection, for both users
Drawbacks
- Contacts are not shared across the two profiles. You should also synchronize your contacts for the second user
- You have to customize the whole second user profile. I would suggest to only use Whatsapp on the second profile and disable/uninstall all other apps
- You have to switch to the second user to see the notifications
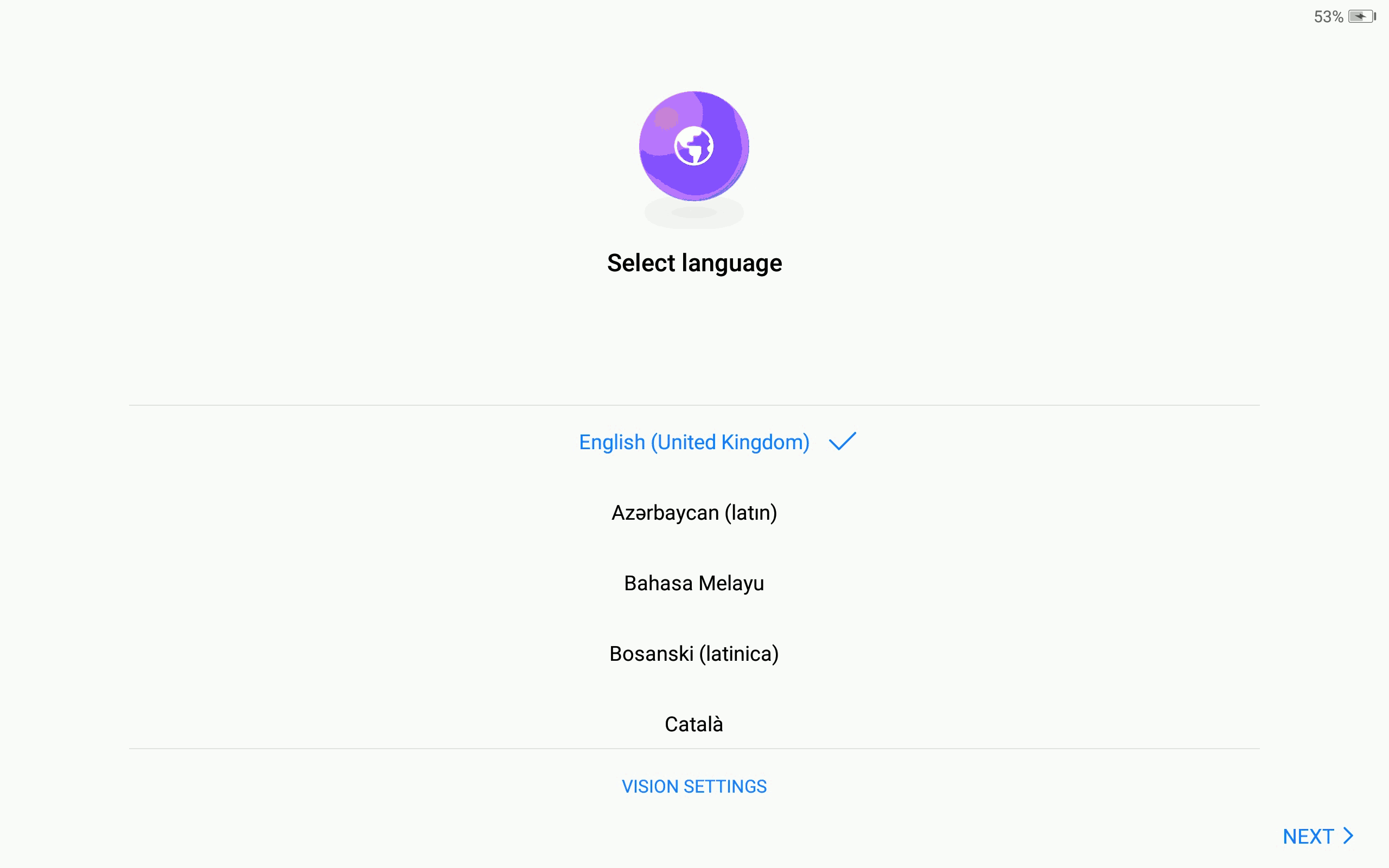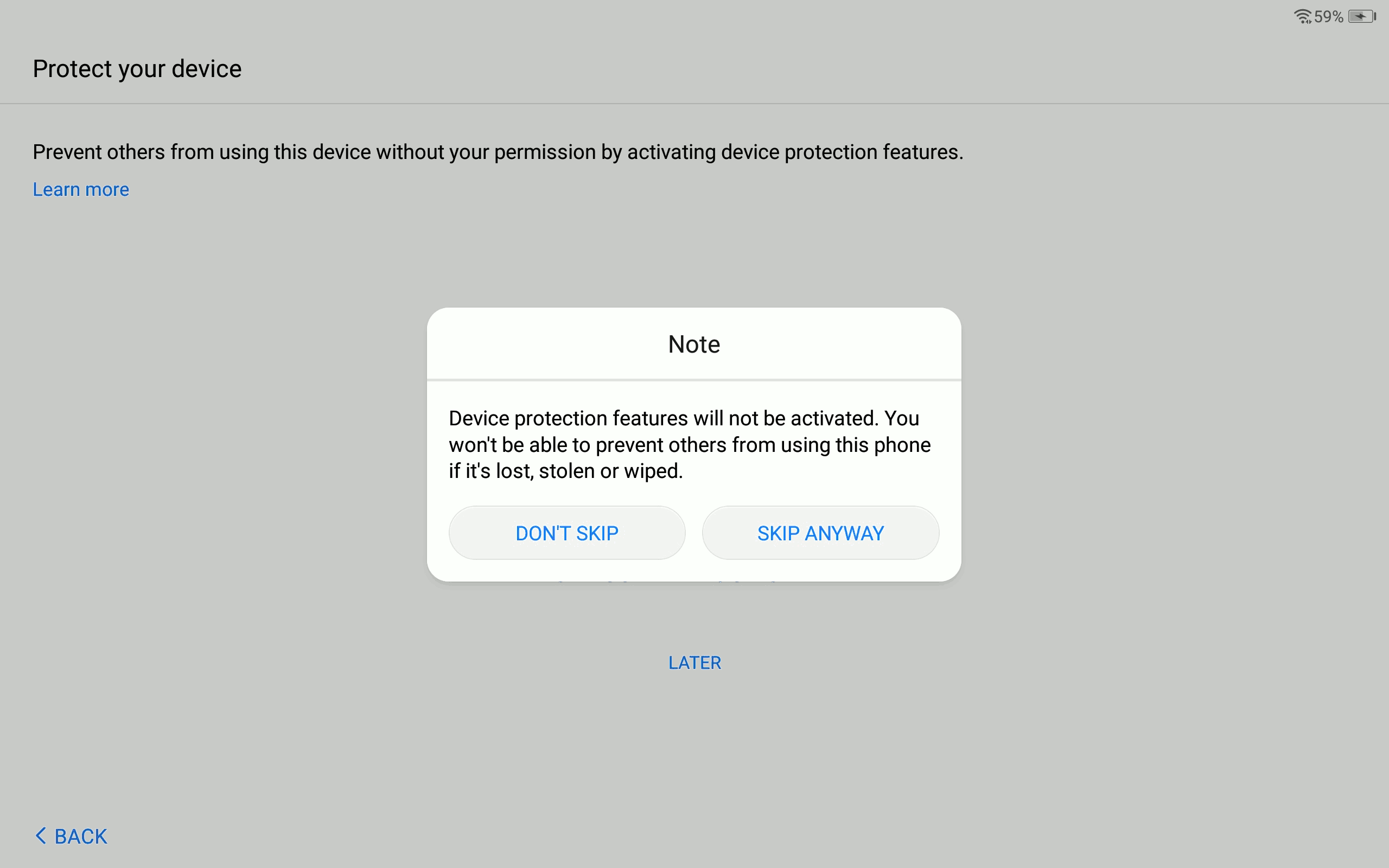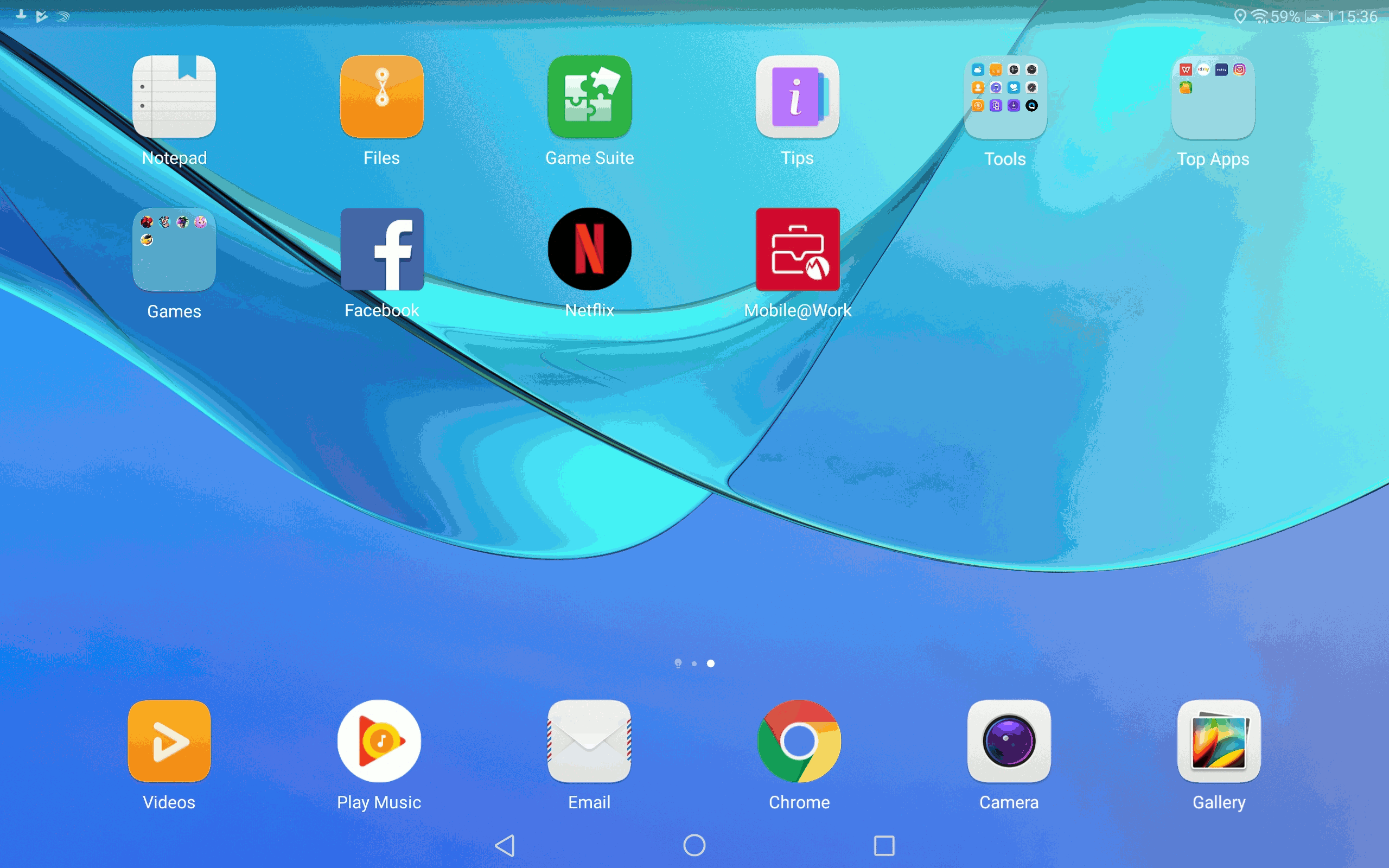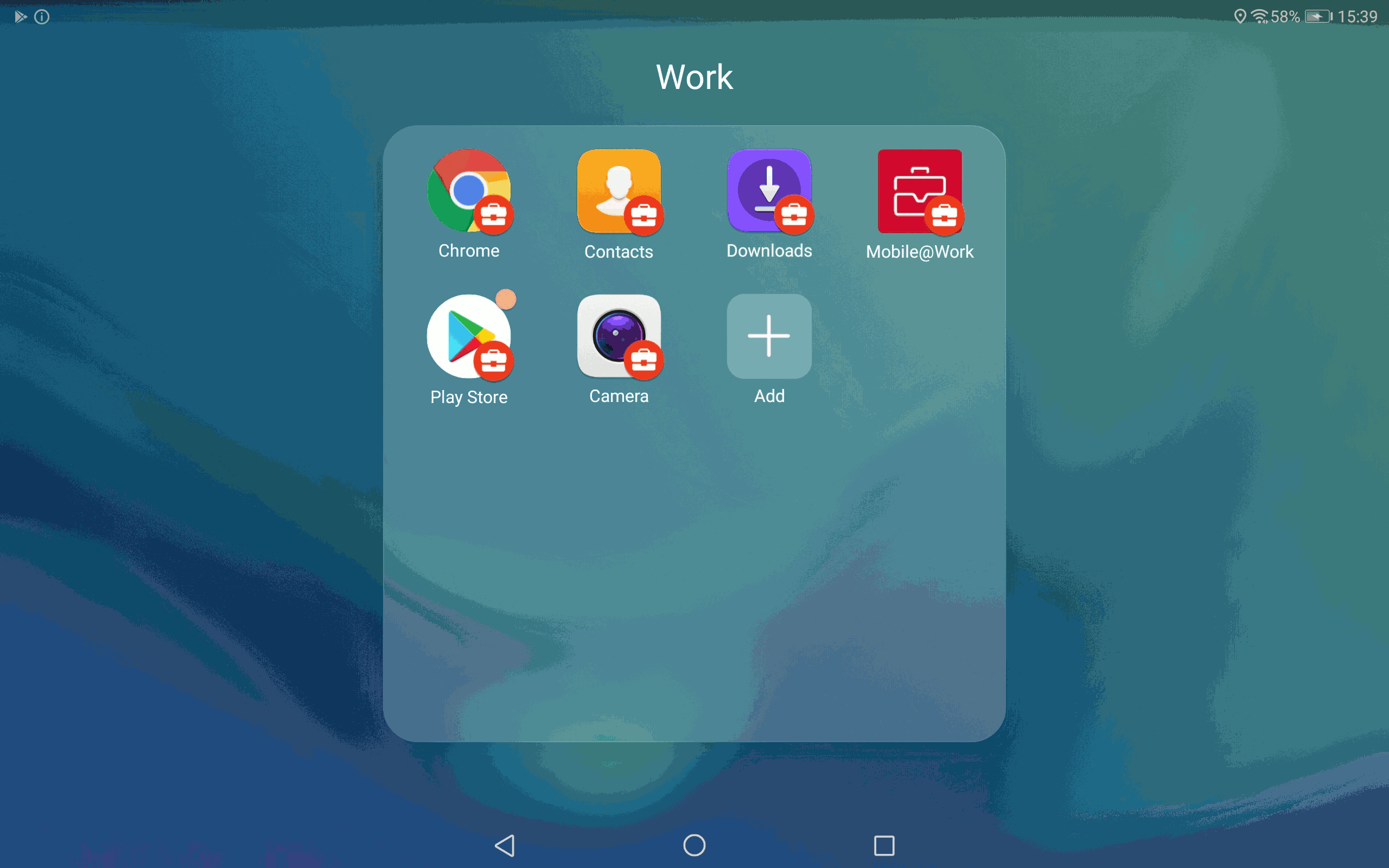
Solution 2: Add a work profile
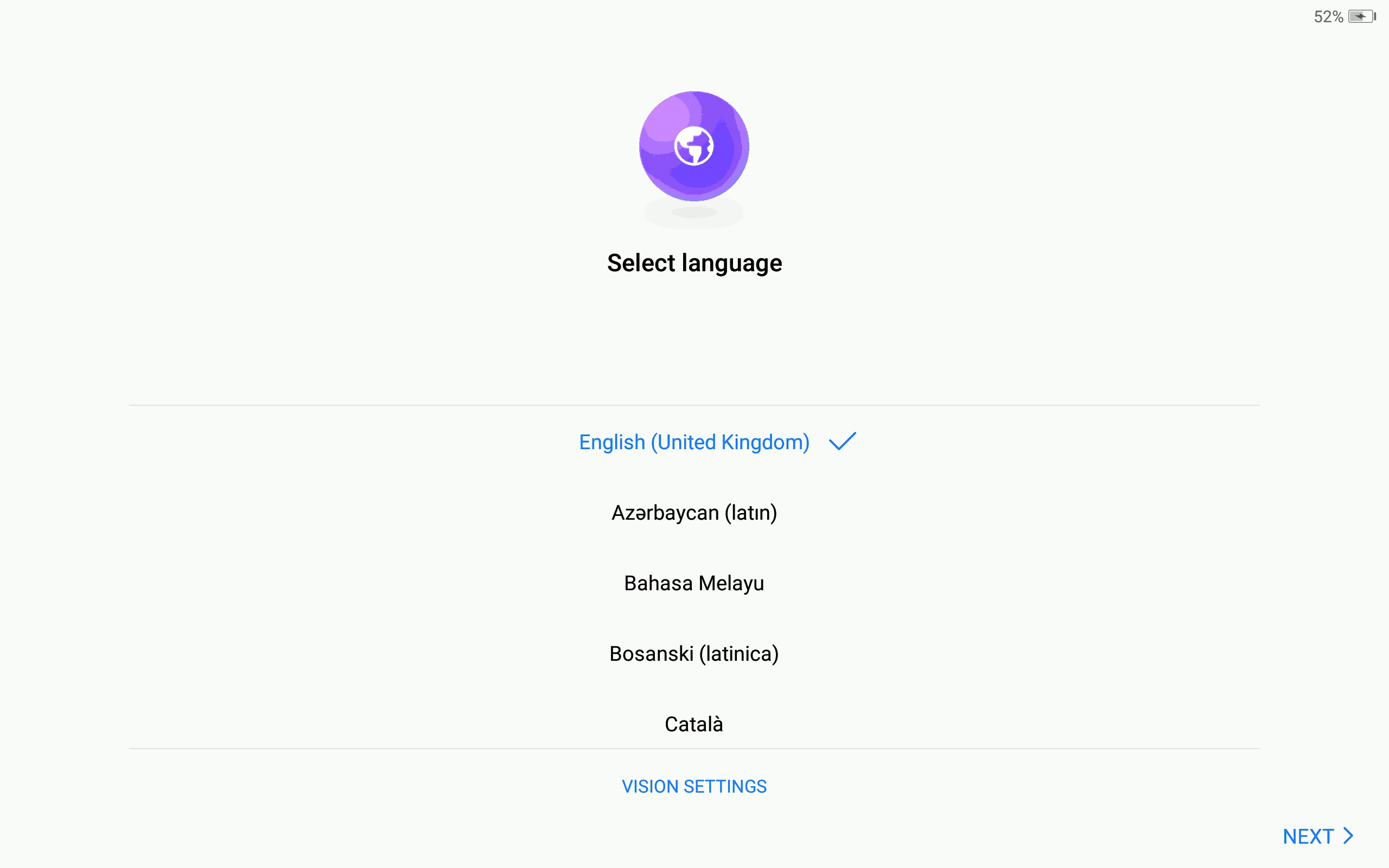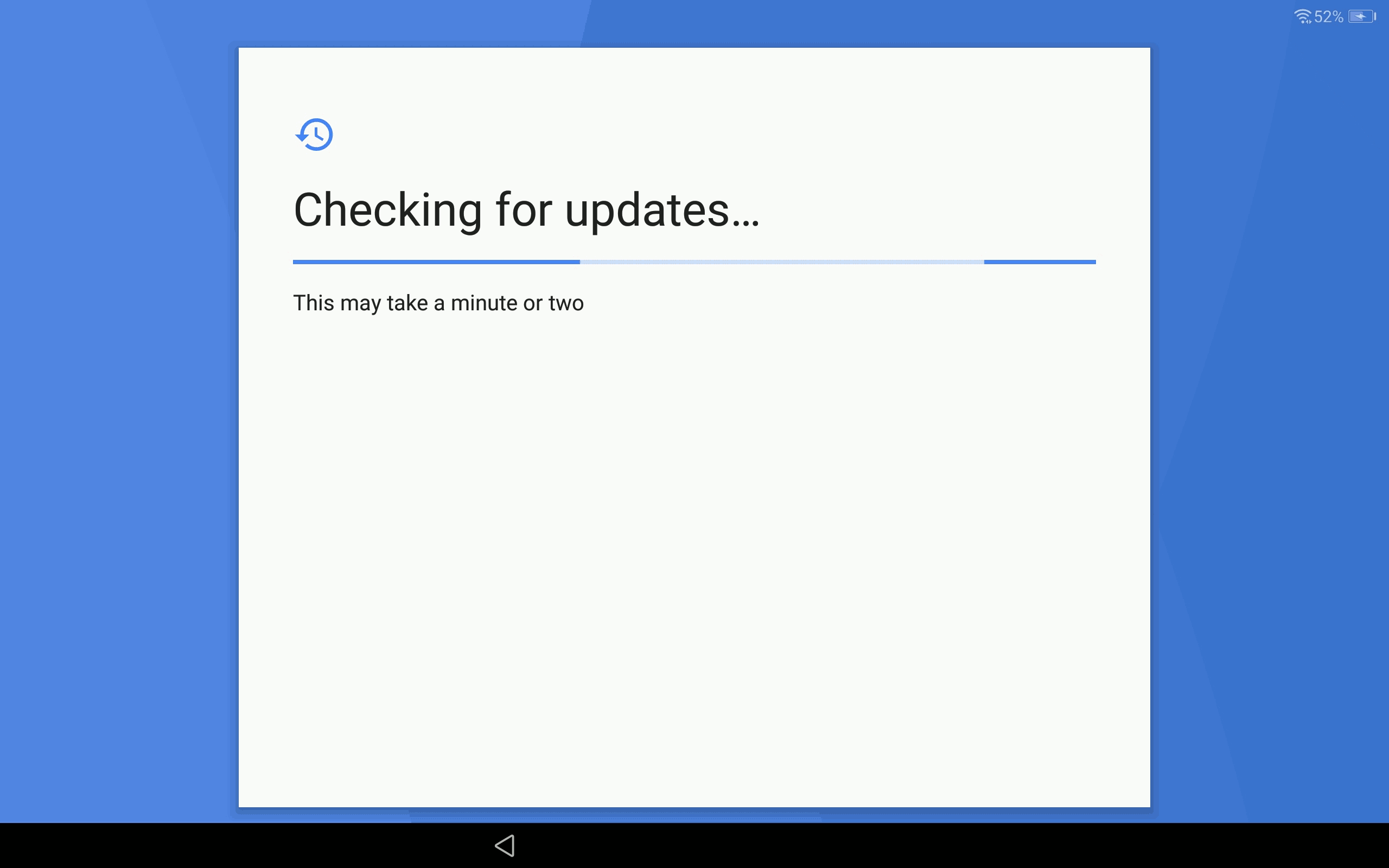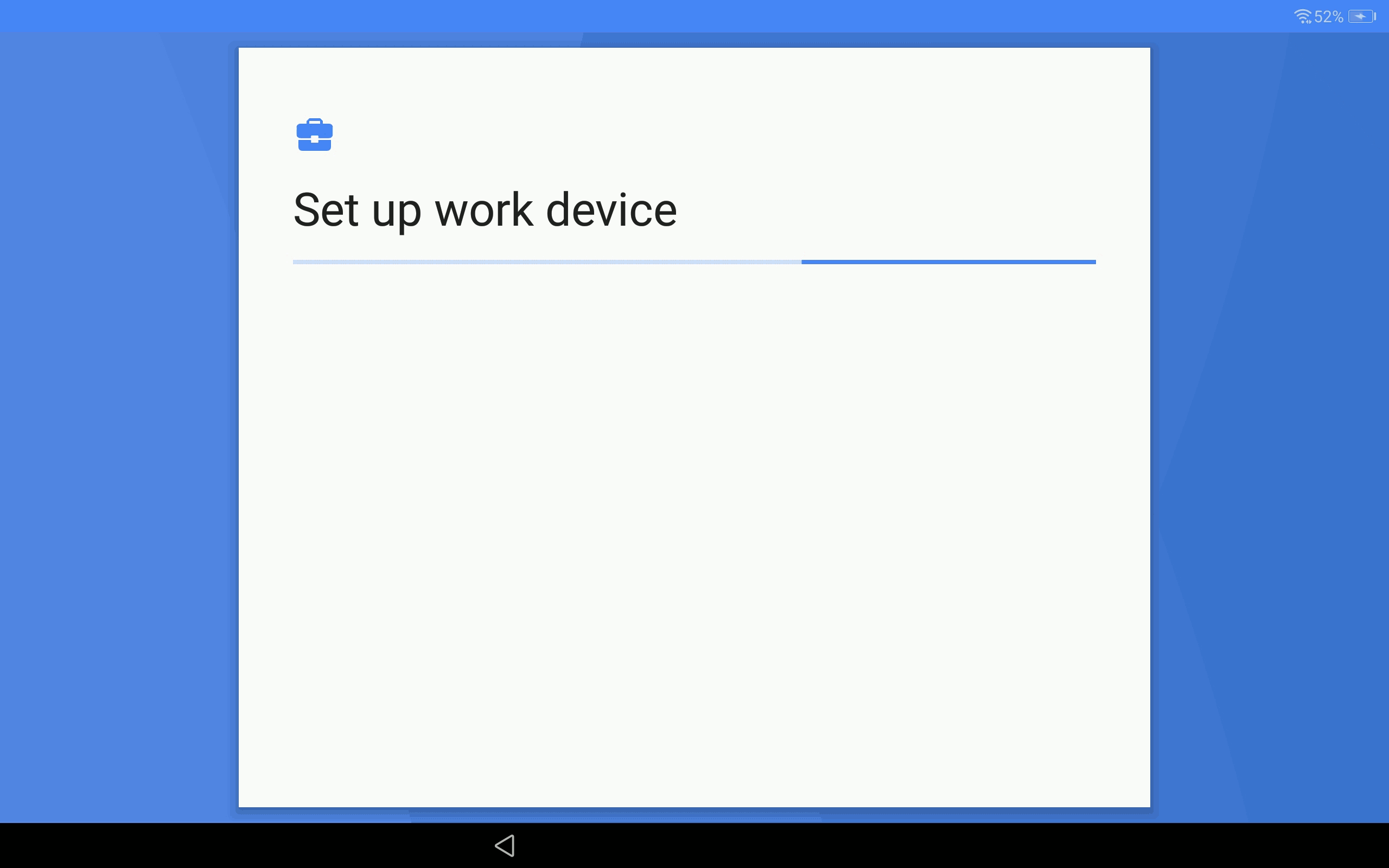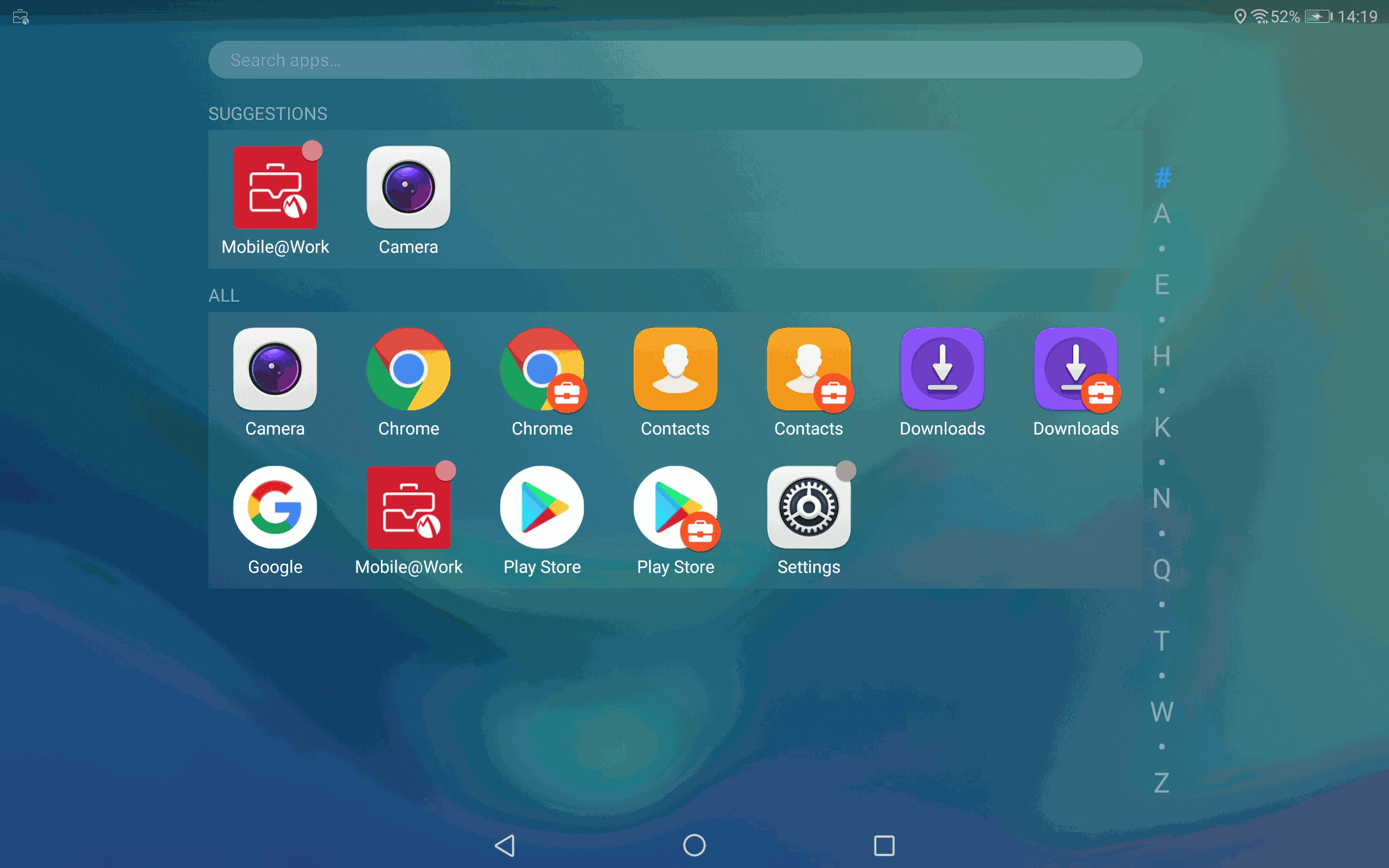
The second solution I have found is even better and works flawlessly. The goal is to setup a Work profile with the TestDPC application from Google, as if you would use a “business profile” on your smartphone. A second Whatsapp will be whitelisted and made available in the work profile.
Step 1: Download the TestDPC application from Google and setup a work profile.
https://play.google.com/store/apps/details?id=com.afwsamples.testdpc&hl=en_US
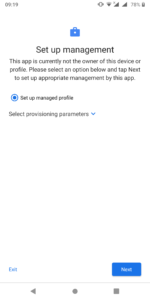
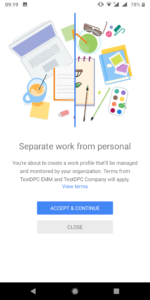
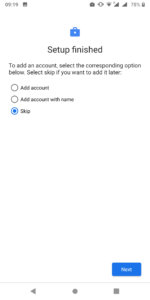


Step 2: Whitelist Whatsapp
Open the badged version of Google Play (in the work profile), add a Google Play account and proceed with the standard activation. You will have two Whatsapp activated: the application in the private profile and the Badged version in the work profile.

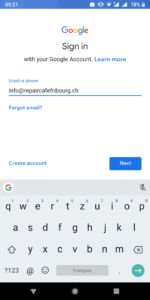
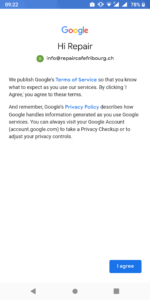



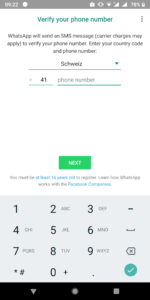


On Samsung smartphones, you will find the “work profile” in the “Workspace directory”.
Advantages
- The two Whatsapp apps can be accessed quickly
- Notifications are working for both apps without switching the user
- You could even protect the access to the work profile with a PIN code in the work profile settings.
Drawbacks
- This method does not work if your device already has a work profile (MDM registration from your Company with Android Enterprise)
- Contacts are not synced between the personal and business space.
- Data exchange between the private profile and work profile might be limited, depending on the settings you have in the TestDPC application. Media received in the work profile will not appear in the photo, video application of the personal space. You may have to download more application in the “business” profile to actually play videos, enable a gallery app etc.
- Warning: if you remove the work profile, all business data will be wiped and you will lose the Whatsapp data for the work profile (messages, images etc.)
The TestDPC application offers many other settings – explaining them is out of scope of this blog article. However, feel free to post a comment on this thread if you have a question!
Other solutions
Some manufacturers proposes a “Dual mode” for applications like Whatsapp. This is of course the best solution.

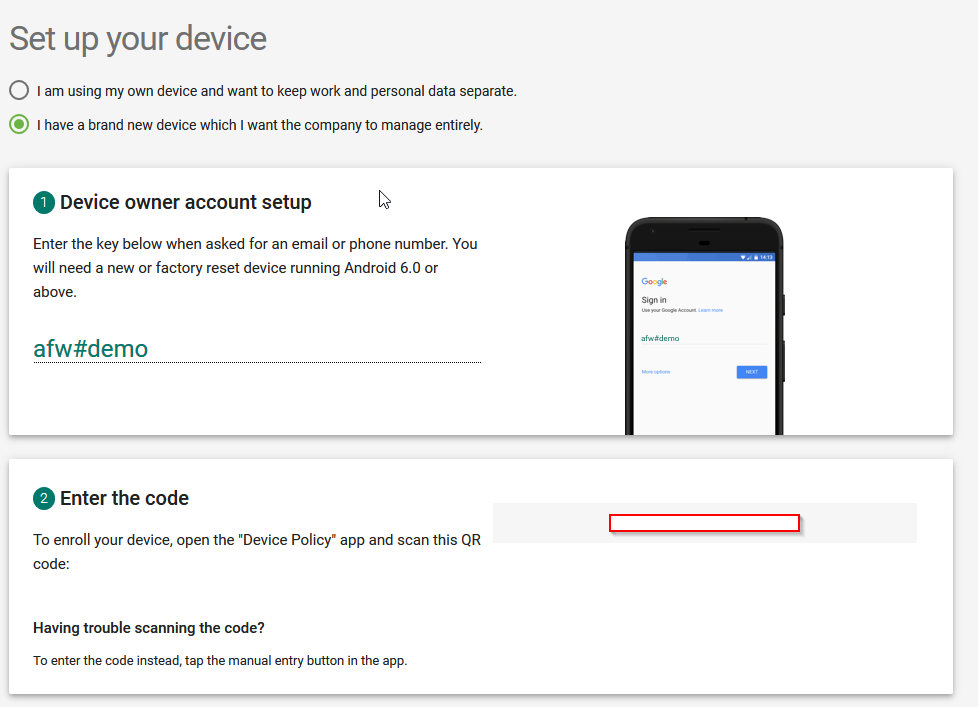




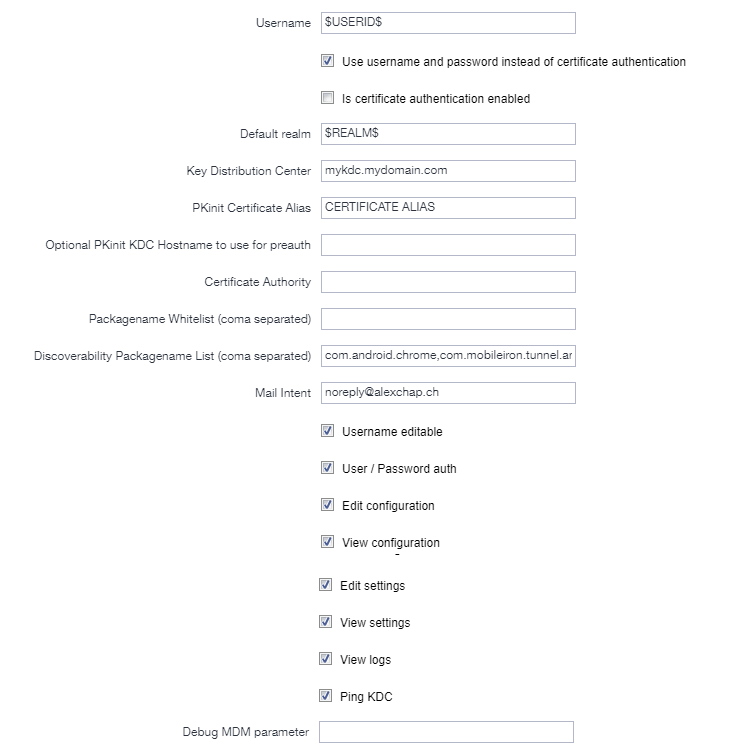
 Single-Sign on has always been a challenge on mobile phones. Now that companies have to switch to Android Enterprise (Device Admin’ is being deprecated), the Android world is kind of lacking an important feature which used to work with EMM Proprietary solution: Native Kerberos SSO or Kerberos Constrained Delegation.
Single-Sign on has always been a challenge on mobile phones. Now that companies have to switch to Android Enterprise (Device Admin’ is being deprecated), the Android world is kind of lacking an important feature which used to work with EMM Proprietary solution: Native Kerberos SSO or Kerberos Constrained Delegation.